Leverage Threat Intel Reports
-
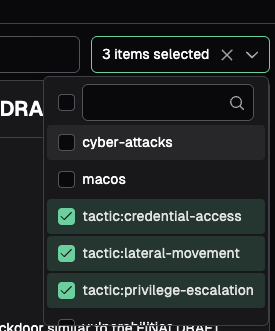
Nebulock curates an open source feed of threat intelligence articles, focusing on the MITRE tactics of of Credential Access, Lateral Movement, and Privilege Escalation. These reports are tagged by MITRE tactic, operating system, and severity. You can filter by tag or search by keyword to find threat reports of interest to you.
-
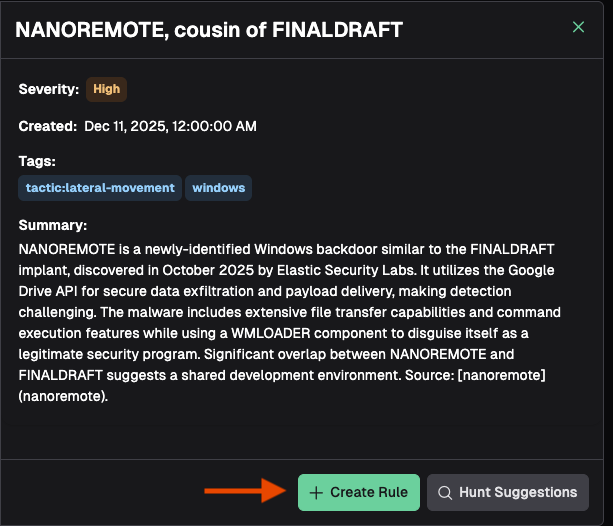
Once you’ve identified a piece of relevant threat intelligence, view a quick summary of the report. You now have the option to use this threat intelligence to create a Detection Rule or start a Vibe Hunt.
-
Clicking Create Rule opens a dialogue box. Ensure you select the proper log source, and provide any extra context for the rule agent in the text box. Clicking Start Rule Generation will prompt the rule agent with the threat intelligence article and the context you entered into the text box. Proceed with the rule creation process as outlined in Write Your First Detection Rule.
-
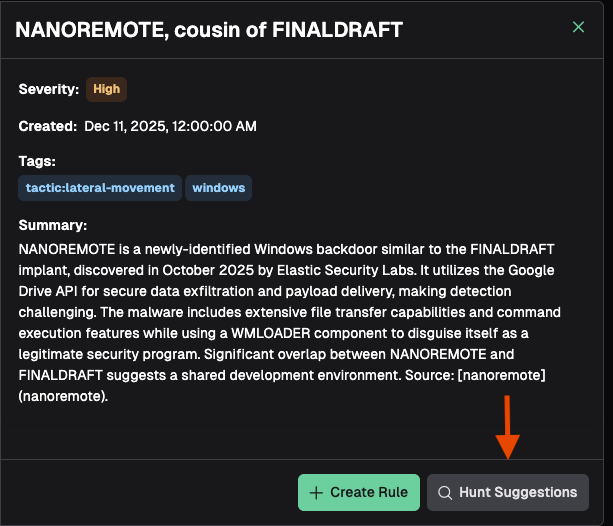
Clicking Hunt Suggestions will kick off an agentic workflow to generate three hunt suggestions based on the threat intelligence article. Once complete, the hunt suggestions will be presented and you can click on the one that is the most relevant. Doing so will launch you into the vibe hunt workflow as described in **Vibe Hunting **.
-
Updated about 2 months ago
